
October 2021
Summary
 Together with food safety and food fraud, food defence forms the food protection ‘umbrella’ of food safety management systems. Food defence programmes protect food from intentional contamination through the use of biological, chemical, physical or radionuclear agents which would not normally be found in that food or its processing environment. Plans for food defence focus on facility, operational, cyber and personnel security, with the goal of preventing deliberate attacks on the food supply chain by malicious, criminal or terrorist threats and activities. Originating in the United States, food defence programs are a part of Global Food Safety Initiative (GFSI) certification and are mandated in the supply chain by companies such as Kellogg's, Kraft, Marks and Spencer and Tesco.
Together with food safety and food fraud, food defence forms the food protection ‘umbrella’ of food safety management systems. Food defence programmes protect food from intentional contamination through the use of biological, chemical, physical or radionuclear agents which would not normally be found in that food or its processing environment. Plans for food defence focus on facility, operational, cyber and personnel security, with the goal of preventing deliberate attacks on the food supply chain by malicious, criminal or terrorist threats and activities. Originating in the United States, food defence programs are a part of Global Food Safety Initiative (GFSI) certification and are mandated in the supply chain by companies such as Kellogg's, Kraft, Marks and Spencer and Tesco.
Introduction
Whereas food safety ensures that food is as safe as possible, so that consumers will not be harmed by accidental contamination or foodborne illness when the food is prepared and eaten according to its intended use(1), food defence is a separate area that addresses food system vulnerabilities (physical, personnel and operational security) to prevent deliberate attacks on food by malicious, criminal or terrorist threats or activities(3), with the goal of reducing the impact of any potential system attacks or disastrous events(4).
Using Good Agricultural Practice, Good Manufacturing Practice (GMP), HACCP and other food safety systems, threats to food safety can often be reasonably anticipated. This is not the case with food defence as it is likely that threats will frequently be unanticipated without intelligent information(5).
The modern food supply is a system of systems that is long and sophisticated, and therefore provides numerous opportunities for deliberate contamination at production, processing, retail and foodservice stages. The swiftness, complexity and global nature of food manufacture and distribution means that foodborne illness can be difficult to: detect (leading to multi-country outbreaks); investigate (2011 outbreak, Germany - E. coli O104:H4 in fenugreek sprouts); and extremely difficult to control. Deliberately contaminated food could cause morbidity and/or morality on a global scale. A robust food defence plan can help to facilitate a rapid response if an incident occurs (6).
The food sector is also lucrative, with data from the Department for Environment, Food & Rural Affairs (DEFRA) apportioning over £120 billion national Gross Value Added (in 2018), 4.1 million people being employed (in 2019) in the food sector, and customer expenditure (in 2019) being £234 billion on food, drink and catering (7). As such, targeting the food chain has health, societal, psychological, economic and political significance.
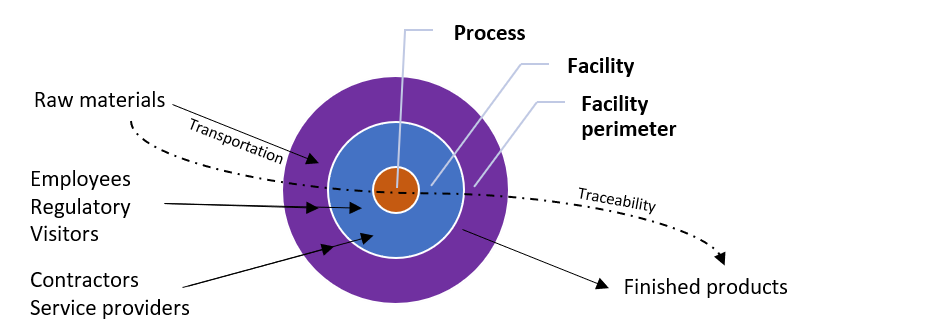
The aim of a food defence plan is to prevent an incident or attack. If an incident does take place, to be able to respond rapidly and efficiently and to enable rapid recovery and restore consumer confidence in the supply chain. It focuses on layers of defence including the site perimeter, buildings and the processes designed to prevent food contamination.
In 2002, World Health Organization (WHO) said that ‘the malicious contamination of food for terrorist purposes is a real and current threat, and deliberate contamination of food at one location could have global public health implications’ (6). The same year, the World Health Assembly also expressed concerns about threats to the general population by the intentional use of agents in food (8). In the Elliott Review (9) into the integrity and assurance of food supply networks, Professor Elliot states that ‘food crime is an emerging issue for all of Europe’, although it is not possible to know whether this is due to individuals, groups or organised criminal gangs. In 2004, former American Secretary of Health and Human Services, Tommy Thompson, said ‘for the life of me, I cannot understand why terrorists have not attacked our food supply, because it is so easy to do’.
Of all industrial or infrastructure-related activities, the food supply is the most complicated system in the world. It is a fairly easy target and with a potentially high number of people that would be impacted, with those foods that have a uniform distribution, short shelf life (rapid distribution and consumption by consumers), reach key populations or are made in large batches, being particularly vulnerable to intentional contamination. Modern bioterrorism attacks on the food chain could be conducted for personal or business extortion, financial gain through counterfeiting, political influence, corporate sabotage or destruction of a brand or company image, and/or destruction of an economic sector. Materials reportedly discovered in Al Qaeda training camps in Afghanistan showed that the group had knowledge and potential to be able to contaminate the food supply (10) and a cell of Jamaah Ansharut Daulah, in Indonesia, plotted a suicide attack utilising abrin(11) (a natural poison extracted from the seeds of the rosary pea) - which could also be used to contaminate food. However, there have been few terrorist attacks on food reported to date (12) and given the history of incidents it is more likely that a threat to an organisation will come from an ‘insider’.
Deliberate contamination of food products can have public health consequences (on the population and resources available to deliver healthcare), widespread public fear, economic impacts for food manufactures and countries (foodborne illness is very costly), disruption of trade, a loss of confidence in the safety of food by consumers and a loss of confidence in the government. Intentional adulteration of food can be difficult to anticipate and prevent, plus is designed to evade detection. Contaminants may often be unconventional.
Intentional food contamination and terrorism is not a modern phenomenon; ancient Rome had regulation around the adulteration of wine; Emperors and Kings had personal tasters to taste the food first; Europe introduced laws to protect consumers in the 13th century; the German beer purity law was introduced in 1516 and in the 19th century strychnine in rum and beers, red lead in Gloucester cheese to give a good red colour, arrowroot in cream to thicken it, turmeric in Chinese tea, milk containing water or chalk, sawdust in ice cream and copper in butter were amongst other contaminants used to adulterate food (13).
Examples of historic food contamination:
Year |
Country |
Agent |
Product |
Reason |
|
1959 |
Morocco |
Jet engine lubricating oil |
Cooking oil |
Deliberate contamination |
|
1970 |
Canada |
Ascaris suum |
Food |
Student tainted their roommate’s food |
|
1978 |
Netherlands & West Germany |
Mercury |
Israeli citrus |
Terrorists targeting Israeli economy |
|
1981 |
Spain |
Colza oil |
Olive oil |
Economics |
|
1984 |
USA |
Salmonella |
Salad bars |
Rajneeshee religious group hoping to disrupt local election |
|
1984 |
Japan |
Cyanide |
Confectionary |
Attempt to extort money from a manufacturer |
|
1985 |
Austria |
Diethylene glycol |
Wine |
Fraud - wines appeared sweeter and more full bodied |
|
1996 |
USA |
Shigella dysenteria |
Food |
Disgruntled laboratory worker |
|
2001 |
China |
Rat poison |
Noodles |
Owners of factory reportedly laced food |
|
2002 |
China |
Rat poison |
Breakfast foods |
Owner of fast food outlet sabotaged competitors products |
|
2003 |
USA |
Insecticide |
Ground beef |
Supermarket employee to get supervisor in trouble |
|
2016 |
Pakistan |
Sweets |
Pesticide |
Family dispute |
|
2017 |
Germany |
Ethylene glycol |
Baby food jars |
Attempt to extort money |
|
2018 |
Australia |
Sewing needles |
Strawberries |
Product tampering |
|
2019 |
USA |
Eggs/chicken |
Bleach |
Product tampering |
With the global nature and length of the supply chain, food manufactured in one country can have a large effect on others. There are a wide variety of hazards that can be considered in food defence, which can be broken down into biological, chemical, physical and radio-nuclear hazards.
In food defence there may be no direct precedent from which to learn, statistics may be immaterial and it unlikely that there will be any environmental or ecological principles which can be used. The size of the threat depends upon:
- motivation, innovation and capability of the would-be attacker
- vulnerability of the site or process targeted
- prospective impact of a successful attack.
- Biological
Delivery through food to cause disease by biological agents in liquid, solid or aerosol form. Can be achieved by utilising an animal or plant variety to destroy crops and livestock for political or economic means. Biological agents could be used to cause foodbourne illness. Potential agents include Salmonella and Listeria which could cause mass human casualties, and Vibrio cholera which can also cause severe economic loss.
- Physical
Diabetic needles, sewing needles and glass have been used to deliberately adulterate food products. In 2005, bread was found in to be contaminated with glass and needles, in UK. Tampering incidents are often not widely published by regulatory bodies for fear of copycats. Physical hazards can also include damage to infrastructure or equipment.
- Chemical
A wide range of chemical agents that are likely to cause foodborne illness, and could be used to intentionally adulterate food, includes agri-chemicals such as insecticides, poisons (cyanide or strychnine), melamine and naturally occurring toxins (e.g. from poisonous mushrooms) could be used to adulterate food. In 1980, in Pittsburgh (USA), a town’s water supply was intentionally contaminated with pesticide. The water supply had to be shut down for two weeks and water was brought in for residents (14). Many of the chemicals are odourless, colourless and tasteless so adulteration would not be detected until foodborne illness in consumers occurred.
- Radio-nuclear
Intentional contamination of radio-nuclear agents through food and drink would be likely to cause widespread panic, prevent the provision of food or water suppliers, or force multiple widescale recalls. An attack of this nature could include long-term contamination of water treatment plants and supply systems, markets, supermarkets and food manufacturing facilities. Given the very large amounts of radioactive material needed, to cause rapid causalities and fatalities, it is likely that an incident of this type would only affect a small number of people (14). In 2006, Alexander Litvinenko was poisoned by Polonium-210 and tests by the Health Protection Agency showed that the poison was in his teacup.
v. Financial
These types of hazards can include the threat, or claim of an attack, commercial espionage and extortion.
i. Motivation
Motivation for intentional or malicious food adulteration may be due to the desire to harm, or kill, as many people as possible (terrorism); be economic, to increase the perceived value of the food, or reduce processing costs; be issue orientated, where an individual or group is trying to damage a brand, company or specific industry, or extortion, where criminals attempt to gain money(15).
ii. Exterior attack
A raw material could be contaminated at the point where it is grown, harvested, distributed or processed. These points may be easier to access than processing facilities, and the contaminated raw materials would enter the downstream supply chain via typical routes: cyberattacks, including viruses which will delete systems, file alteration, using a company’s computer system to attack someone else’s, or stealing confidential information (16).
iii. Forced entry
Where a person (intruder), wishing to intentionally contaminate food, breaks into (makes a new opening into) a facility. Theft of items or vandalism may divert attention.
iv. Covert entry
Individuals or groups utilise stealth and deception to obtain access to the desired facility, such as giving false credentials. For example, a member of an animal rights activists group gaining employment at a slaughterhouse in order to film alleged abuses, an individual posing as a visitor, or reporters entering a processing area without permission, to investigate a story.
v. Insider compromise
In this type of attack, the person uses their genuine access to the raw material, food or information to compromise a food or company.
Where attacks could come from (1-19)
- Disgruntled employees (current or former)
- Protestors or activist groups
- Terrorists
- Subversives
- Competitors
e.g. posing as: cleaning crew, contractors, temporary employees, truck drivers (shipping and receiving), visitors, utility representatives.
- Criminals - computer theft, hacking or denial of service; professional criminals - specific criminal trade, opportunistic or entrepreneurial (counterfeiting, food fraud).
While a food defence plan is in some respects similar to a HACCP plan, it generally should not be managed by a site’s Quality Assurance or Technical Manager, as there can be conflicts between the two plans. The food defence plan should be treated as highly confidential by the site, to avoid giving away the site’s weaknesses and response plans. A food defence plan assesses the current security conditions, and risk mitigation measures already in place, to prevent intentional food contamination and sets out control measures, that have been developed by a team at a specific facility, to prevent intentional adulteration of raw materials and food products. The plan must be developed (assessing where issues may arise and reduce any identified risks), written, implemented, tested, verified and maintained, if it is to be functional and ‘live’ document. Internal and external threats are constantly evolving, so a plan needs to be reviewed frequently. Control measures should be developed by an establishment to prevent intentional adulteration of a product, bearing in mind that zero risk is unachievable. Procedures and policies are people-focused, as malicious intent or act require an individual or group of people. An attacker is likely to want to see a short-term impact (such as with foodborne illness), so long-term effects such as chronic disease are not a major concern. Developing a food defence plan does not require the creation of another HACCP-type document, although does require a vulnerability assessment. A sites current HACCP plan, including Sanitation Standard Operating Procedures (SSOP), GMPs, training, crisis management procedures etc. can be used to help develop a food defence plan.
Step 1 - Food defence assessment
Choose a team to be responsible for the security of your perimeter, facility and processes. To understand which parts of the facility may be more vulnerable to threats, conduct a vulnerability assessment (numerous checklists are widely available on the internet). Potential internal and external threats should be considered.
Step 2 - Develop a food defence plan
Once the areas of vulnerability have been identified (exterior or interior of the site, procedures used on daily operations etc.) identify preventative actions that are cost effective, realistic and based on risk assessment to minimise the vulnerabilities. Receiving, processing, storage and shipping security and water/ice security is the minimum that should be considered.
Step 3 - Implement the food defence plan
The key elements of effective plan implementation are assigning responsibilities (who implements, manages and updates the plan), training staff (in all provisions of the plan, so that employees know their responsibilities), developing contact lists (including police, government and environmental health officials, suppliers, customers), and checking the facility’s recall plan (up to date and tested at a minimum within the last year).
Step 4 - Test the plan
Plans can be tested in a variety of ways, including mock recalls (at the same time as the HACCP plan and food defence), mock incidents/simulations, drills and tabletop exercises. A post-event evaluation, with lessons learned, should be conducted with corrective actions agreed and implemented. Ways to test the plan include: reviewing signage, procedures, inventory, employee access cards and visitor logs.
Step 5 - Manage the plan
Consider how the plan will be managed in the long term. This can include annual reviews and periodic tests, to see if the plan still effectively reduces the risks of intentional contamination, or needs to be updated. Changes to operations, construction work, addition of new technology, a new supplier or raw material, a contamination incident at a competitor, are examples of what should also trigger a review.
A robust food defence plan will typically contain:
- Security management, which should include:
- physical controls that prevent access, such as fences, security guards, turnstiles etc.
- technical controls, including swipe cards, cameras, specialised hardware/software, including firewalls
- administrative controls (policies, procedures).
- Personnel measures including:
- Screening - pre-hiring, hiring, post-hiring
- Daily work assignments - where should operatives be? How do you identify employees with access to certain areas?
- Identification and restricted areas - access identification and security checks, daily work assignments, e.g. what areas should operatives be in and how to identify them?
- Personal items - what are you allowed to bring on site (hunting guns, ammunition, personal medications etc.). Can employees bring portable recording equipment on site?
- Training in food security procedures - everyone should be trained in expectations and empowered to ask people for identification
- Leaving procedures - are access codes changed and entry passes recovered?
- How visitors to the site are identified and accompanied:
- Visitors, including customers, reporters, tour groups, supplier representatives etc.
- Regulatory - health and safety, food safety, labour
- Contractors/service providers e.g. laundry, maintenance contractors, delivery drivers, couriers, pest control representatives
- Facility
- Physical security
- Laboratory safety
- Storage and use of poisonous and toxic chemicals e.g. cleaning and sanitising agents, pesticides
- Storage and items that may be used as physical contaminants: nails, injection needles, blades etc.
- Operations
- Incoming materials and contract operations
- Production processes e.g. weighing, mixing
- Storage
- Security of water and utilities
- Mail packages
- Access to computer systems and prevention of cyber attacks
The UK has identified food as one of the nine sectors characterised as being necessary for the functioning of the country and an essential service upon which the delivery daily life in the UK depends (17, 18, 19). The assessment includes possible casualties, economic and public effects, and the specificities of each sector, as well as existing security solutions for protecting the food supply. The Centre for the Protection of National Infrastructure, in the UK, can utilise resources from other government agencies, including MI5, the Communications-Electronics Security Group and Government departments, responsible for national infrastructure sectors(20,21).
Food Safety Modernization Act
The FDA Food Safety Modernization Act (FSMA) was signed into law on 4 January 2011 and is considered to be the most comprehensive reform of the United States food safety laws in over 70 years. The legislation moves the focus, for regulators, from responding to contamination events to preventing them (22) and includes mitigation strategies to protect food against intentional adulteration.
ISO/PAS 28000:2007, ‘Specification for security management systems for the Supply Chain’
This ISO certification is for all sizes of business, at any stage in the supply chain, and is linked to other business management aspects. It specifies the requirements for a security management system which includes areas critical to the security of the supply chain, and covers financing, manufacturing, information management and facilities (23).
AEO (Authorised Economic Operators)
This certificate is a quality mark internationally recognised as indicating that a company’s international supply chain is secure, and that their customs controls and procedures are proficient and in compliance with the standard. It is not a mandatory certification, but a commercial decision allowing faster access to some simplified customs procedures, and the right to ‘fast-track’ shipments through selected HM Revenue & Customs (HMRC) safety and security procedures, in some cases. The certification standards cover: protection of cargo units, access to shipping areas, loading docks and cargo, safety of goods during manufacture, storage, and transport, security measures with suppliers, security screening on potential employees who would work in security-sensitive positions, and staff training on safety and security policies and procedures (24).
Global Food Safety Initiative (GFSI)
GFSI certification programmes, including BRC and Global Gap, have site security and food defence requirements, including all raw materials that enter the premises, so that an individual cannot sabotage the process (25).
The PAS 96:2017 guide to protecting and defending food and drink from deliberate attack provides some approaches to the potential problems of intentional attack, on the food and drink industry, to help businesses deter potential attackers. It is not a certification, however major UK companies may expect a supplier to comply with the standards set out in the guidance document (26).
FDA’s ‘CARVER plus Shock’ (27) is a method of vulnerability assessment which offensively targets priorities, by breaking down a food system or process into small pieces. The tool helps to identify the vulnerabilities within a system, or infrastructure, to a malicious attack. It gives the food defence team the opportunity to think like an attacker and identify the most attractive targets for contamination. The focus can then be on resources to protect facilities most vulnerable points.
CARVER is an acronym for six attributes are used to evaluate the attractiveness of a target for attack: criticality, accessibility, recuperability, vulnerability, effect and recognisability. A seventh attribute is evaluated in the modified CARVER tool for combined health, economic, and psychological impacts of an attack, or the Shock attributes of a target (CARVER plus Shock).
A ranking scale is used for the attractiveness of facilities, or processes, which may be vulnerable to deliberate contamination, and can be used to help identify where an attack is most likely to occur within a facility.
Threat Assessment and Critical Control Points (TACCP) is a systematic management process aimed at preventing malicious contamination in foods. It is similar to HACCP, in that it is based on risk assessment, however it often needs a wider range of employees to be involved in the process than HACCP, as it includes Information technology and security.
A risk assessment matrix can help to visualise risks by evaluating and prioritising operational risks and assist management decision making. There are several versions including the severity/probablity matrix and 5x5 matrix.
Risk assessment matrix for use in evaluating hazards and threats(28)
|
|
|
Probability of food contamination |
|||||
|
Frequent |
Likely |
Occasional |
Seldom |
Unlikely |
|||
|
A |
B |
C |
D |
E |
|||
Severity |
Catastrophic |
I |
|
|
|
|
|
|
Critical |
II |
|
|
|
 |
|
|
|
Moderate |
II |
|
|
|
|
|
|
|
Negligible |
IV |
|
|
|
|
|
|
|
Risk levels |
|||||||
Red = Extremely High, Amber = High, Yellow = Medium, Green = Low
Severity |
|
|
Catastrophic |
Complete business failure resulting in deaths |
|
Critical |
Major business degradation, resulting in severe illness |
|
Moderate |
Minor business degradation, resulting in minor illness |
|
Negligible |
Less than minor business degradation and no illnesses |
Probability |
|
| Frequent | Often occurrence to individual. Population is continuously exposed |
| Likely |
Occurs several times; population regularly exposed
|
| Occasional | Will occur; sporadically in a population |
| Seldom | May occur; seldom in a population |
| Unlikely | So unlikely and occurs very rarely in population. Assume it will not occur. |
- Complete a self-assessment and use risk and vulnerability assessments
- Establish a food defence team that develops and maintains a food defence plan
- Develop procedures for investigating a food tampering incident or malicious attack
- Compare operations to recommended practices, or standards, such as PAS 96:2010
- Ensure the following are part of the plan (as a minimum):
- prevent intrusion by unauthorised individuals by forced entry or deception
- prevent malicious acts by workers or routine associate
- prevent the return of previously ‘adulterated’ or hazardous products
- enhance the capability to rapidly deal with any alerts or anomalies detected
- training of employees
- Test the food defence plan
- Establish real relationships with local first responders
- Evaluate policies regarding the screening of personnel by outside contractors.
United Nations Food and Agriculture Organization (UN FAO) Recommended International Code of Practice, General Principles of Food Safety. http://www.fao.org/3/y1579e/y1579e02.htm
- Food Safety and Inspection Service. Food Defence and emergency response. http://www.fsis.usda.gov/wps/portal/fsis/topics/food-defense-defense-and-emergency-response
- Security and robustness in food supply chains in the Netherlands, Solyana A. Subuh; Wageningen University, 2008 https://edepot.wur.nl/3783
- Institute of Medicine (US) Forum on Microbial Threats. Addressing Foodborne Threats to Health: Policies, Practices, and Global Co-ordination: Workshop Summary. Washington (DC): National Academies Press (US); 2006. 1. The U.S. Food System. DOI: 10.17226/11745
- USDA Food Defense Guidelines for Slaughter and Processing Establishments. https://www.fsis.usda.gov/wps/wcm/connect/cd18dfb5-9443-42f8-b8c5-cadf862fcbc4/SecurityGuide.pdf?MOD=AJPERES
- National Statistics Food Statistics in your pocket: Summary August 2020.
- World Health Organisation (WHO), 2003. Terrorist threats to food: guidance for establishing and strengthening prevention and response systems https://apps.who.int/iris/handle/10665/42619
- Elliott Review into the Integrity and Assurance of Food Supply Networks – Final Report ‘A National Food Crime Prevention Framework’, July 2014. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/350726/elliot-review-final-report-july2014.pdf
- Food Defense: International Collaboration in a Critical Area of Biodefense. Marc L. Ostfield (Senior Advisor for Bioterrorism, Biodefense, and Health Security), Remarks to the European Institute: Transatlantic Dimensions of Biodefense Cooperation and Collaboration Event
Washington DC, 2006. https://2001-2009.state.gov/g/oes/rls/rm/2006/77206.htm - Biological Terrorism in Indonesia, V. Arianti, 2019. https://thediplomat.com/2019/11/biological-terrorism-in-indonesia/
- Wohl, Anthony S. Endangered Lives: Public Health in Victorian Britain. Cambridge: Harvard UP, 1983. ISMB 10: 0674252411.
- Veiga, A. S. (2011). Food Defence and Security: The New Reality. In H. Alpas, Berkowicz, M. M. S., & I. Ermakova (Eds.), Environmental security and ecoterrorism (pp. 39-54). (NATO Science for Peace and Security Series C: Environmental Security). Dordrecht: Springer Netherlands. https://doi.org/10.1007/978-94-007-1235-5_4.
- G.R. Dalzeil, ‘1950-2008: A Chronology and Analysis of Incidents Involving the Malicious Contamination of the Food Supply Chain’. CENS, Singapore, 2009. http://www.rsis.edu.sg/cens/publications/reports/RSIS_Food%20Defence_170209.pdf
- Threats to Food and Water Chain Infrastructure NATO Science for Peace and Security Series C: Environmental Security 2010, pp 3-14 Radio nuclear Material Agents that Could be Used in Food and Water Supply Terrorism, Virginia Koukouliou.
- US Food and Drug Administration, Food Defence 101, https://www.fda.gov/food/food-defense-tools-educational-materials/food-defense-101-front-line-employee
- Department of Homeland Security Ready.Gov. Cyber attack.
- Food Safety Magazine, April/May 2008, Risk Management: The Value of the Food Defence Plan, pp 16-21
- European Security Strategy. Secure Europe in a Better World https://www.consilium.europa.eu/media/30823/qc7809568enc.pdf
- 2007/124/EC, Euratom: Council Decision, February 2007 establishing for the period 2007 to 2013, as part of General Programme on Security and Safeguarding Liberties, the Specific Programme Prevention, Preparedness and Consequence Management of Terrorism and other Security related risks. https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=celex:32007D0124
- Communication from the Commission on a European Programme for Critical Infrastructure Protection. Brussels, 12.12.2006 COM(2006) 786 final https://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=COM:2006:0786:FIN:EN:PDF
- Centre for the Protection of National Infrastructure (CPNI) https://www.cpni.gov.uk/critical-national-infrastructure-0#sthash.NfPnzlNO.dpuf
- FDA Food Safety Modernization Act (FSMA) http://www.fda.gov/Food/GuidanceRegulation/FSMA/default.htm
- ISO 28000: 2007 Specifications for security risk management systems for the supply chain http://www.iso.org/iso/iso_catalogue/catalogue_ics/catalogue_detail_ics.htm?csnumber=44641
- HM Revenues and Customs, Economic Authorised Operator http://customs.hmrc.gov.uk/channelsPortalWebApp/channelsPortalWebApp.portal?_nfpb=true&_pageLabel=pageVAT_ShowContent&id=HMCE_PROD1_027618&propertyType=document%23P57_7211%23P167_24709#P339_45765
- GlobalG A.P. https://database.globalgap.org/academy/data/gglive/lm_data/lm_3917/eCourse_AllFarmBase/html/13_01_FoodDefense.html
- PAS 96:2017 Guide to protecting and defending food and drink from deliberate attack. ISBN 978 0 580 98099 2. https://www.food.gov.uk/sites/default/files/media/document/pas962017_0.pdf
- Food and Drug Administration CARVER + Shock Primer http://www.fda.gov/Food/FoodDefense/FoodDefensePrograms/ucm376791.htm
- Karen Constable, November 2019. Vulnerability Assessments https://www.foodfraudadvisors.com/food-vulnerability-assessment-how/
Graphic: Chain by Adrien Coquet from the Noun Project. Apple by Olga from the Noun Project
Institute of Food Science & Technology has authorised the publication of this Information Statement on Food Defence.
This is an update to the Information Statement that has been prepared by Julie Ashmore FIFST. It has been peer-reviewed and approved by the IFST Scientific Committee and is dated October 2021.
The Institute takes every possible care in compiling, preparing and issuing the information contained in IFST Information Statements, but can accept no liability whatsoever in connection with them. Nothing in them should be construed as absolving anyone from complying with legal requirements. They are provided for general information and guidance and to express expert professional interpretation and opinion, on important food-related issues.



